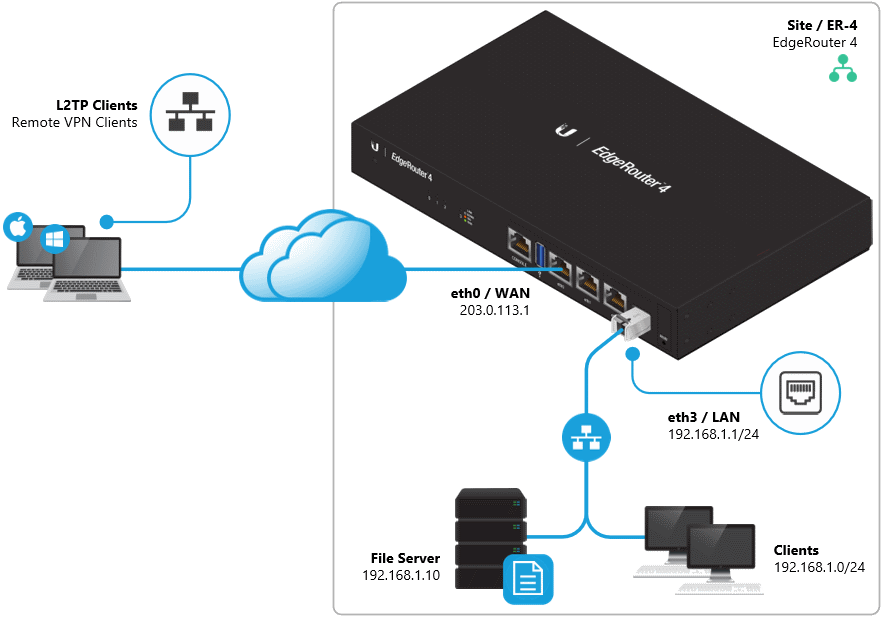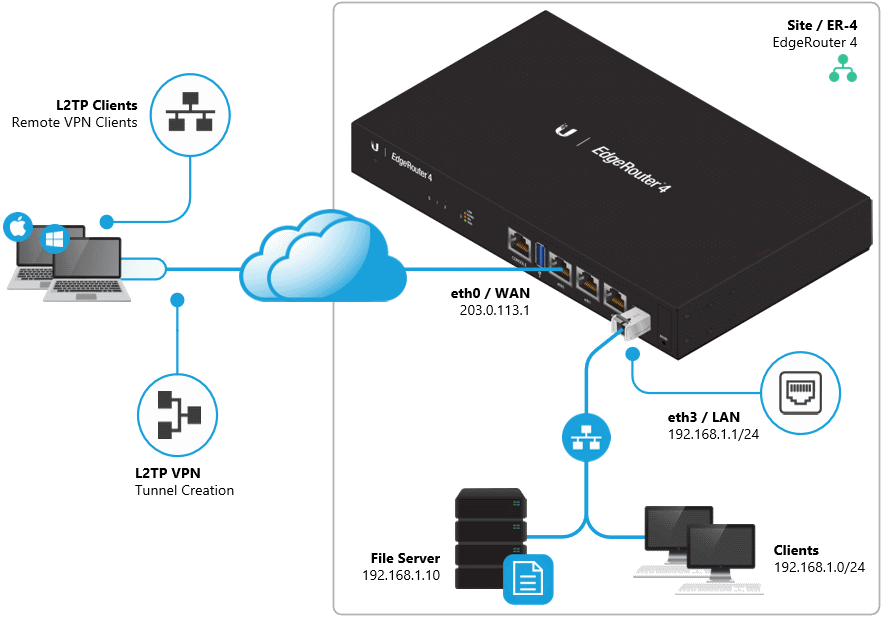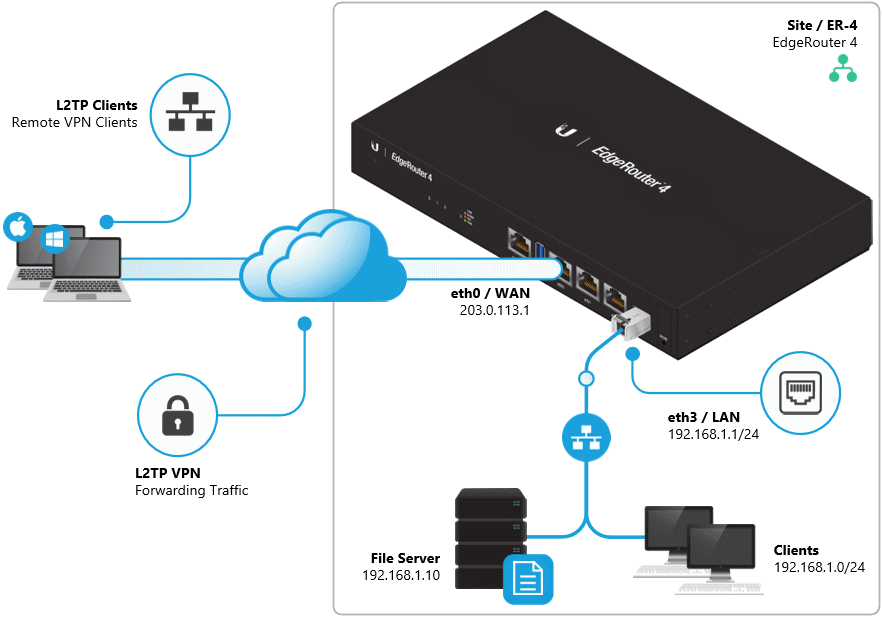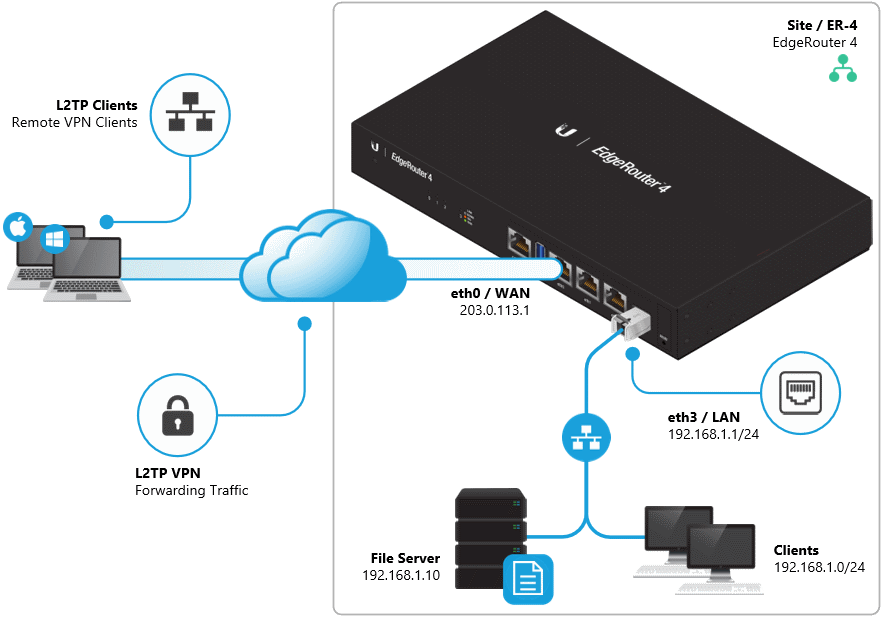
Ubiquiti Edgerouter Remote VPN/L2TP client configuration on IPv4 using radius authentication.
Ubiquiti does not (yet) support IPv6 L2TP.
References taken from ubiquiti site -> link
Step 1: Open Firewall
In order for remote systems to be able to start L2TP/VPN sessions, you must open the firewall on the EdgeRouter for IPSEC/L2TP traffic.
set firewall name WAN_LOCAL rule 110 action accept set firewall name WAN_LOCAL rule 110 description ike set firewall name WAN_LOCAL rule 110 destination port 500 set firewall name WAN_LOCAL rule 110 log disable set firewall name WAN_LOCAL rule 110 protocol udp set firewall name WAN_LOCAL rule 111 action accept set firewall name WAN_LOCAL rule 111 description esp set firewall name WAN_LOCAL rule 111 log disable set firewall name WAN_LOCAL rule 111 protocol esp set firewall name WAN_LOCAL rule 112 action accept set firewall name WAN_LOCAL rule 112 description nat-t set firewall name WAN_LOCAL rule 112 destination port 4500 set firewall name WAN_LOCAL rule 112 log disable set firewall name WAN_LOCAL rule 112 protocol udp set firewall name WAN_LOCAL rule 113 action accept set firewall name WAN_LOCAL rule 113 description l2tp set firewall name WAN_LOCAL rule 113 destination port 1701 set firewall name WAN_LOCAL rule 113 ipsec match-ipsec set firewall name WAN_LOCAL rule 113 log disable set firewall name WAN_LOCAL rule 113 protocol udp
Step 2: Configure L2TP
The following options will configure L2TP with radius integration (mode radius), remember to define the approriate radius server, radius secret key, dns server, client pools, etc.
In this example we are using a pre-shared-secret key for authentication, you can also change this to support x509 certificates for extra security layer.
set vpn ipsec nat-traversal enable set vpn l2tp remote-access ipsec-settings authentication mode pre-shared-secret set vpn l2tp remote-access ipsec-settings authentication pre-shared-secret <pre-shared-key> set vpn l2tp remote-access authentication mode radius set vpn l2tp remote-access authentication radius-server v.x.y.z key <radius-key> set vpn l2tp remote-access authentication radius-server v.x.y.z key <radius-key> set vpn l2tp remote-access authentication require mschap-v2 set vpn l2tp remote-access dns-servers server-1 v.x.y.z set vpn l2tp remote-access dns-servers server-2 v.x.y.z set vpn ipsec ipsec-interfaces interface pppoe0 set vpn l2tp remote-access mtu 1024 set vpn l2tp remote-access outside-address <your public ip> set vpn l2tp remote-access client-ip-pool start <start ip> set vpn l2tp remote-access client-ip-pool stop <end ip>
Step 3: Configure Windows NPS (Radius)
Instead of using local users for VPN authentication, it is also possible to authenticate with a Radius server. In this guide we will describe how to configure Windows Network Policy Service (NPS) to provide the authentication with Active Directory and specific groups.
Once your clients are registered as a Radius Client with the appropriate radius key, create a “Connection Request Policy” using the following options:
- Name: EDGEROUTER-L2TP-VPN
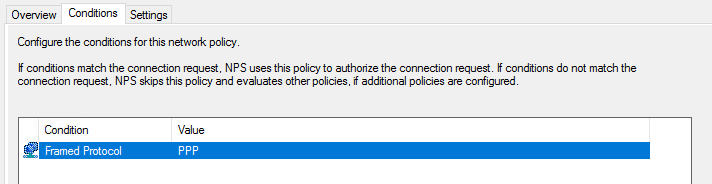
- Condition #1: Framed Protocol : PPP
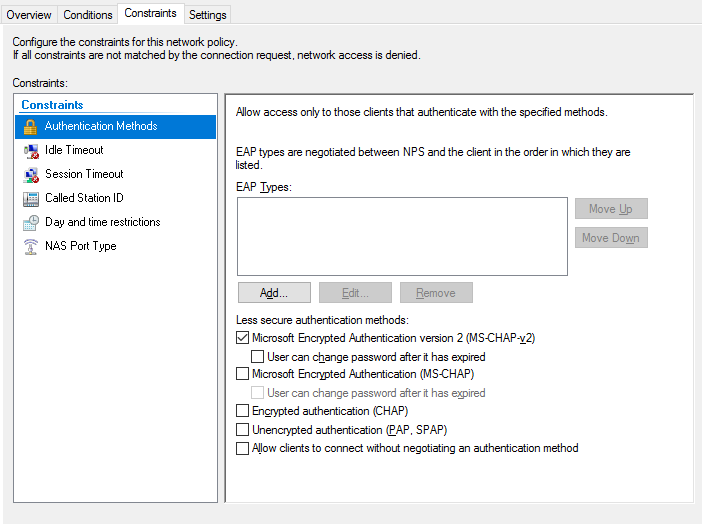
- Constraints – Authentication Methods : Make sure only MS-CHAP-v2 is selected
Once the request policy is created, create a “Network Policy” using the following options:
- Name: EDGEROUTER-L2TP-VPN
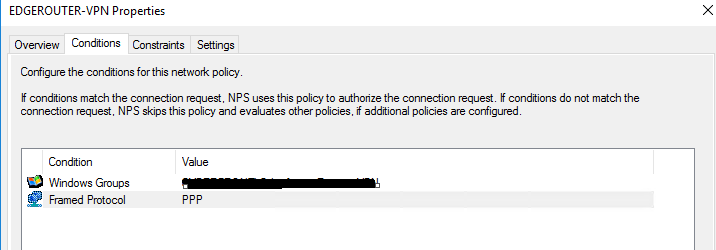
- Condition #1: Framed Protocol : PPP
- Condition #2: Windows Group -> Define your windows user group that requires access
- Constraints – Authentication Methods : Make sure only MS-CHAP-v2 is selected
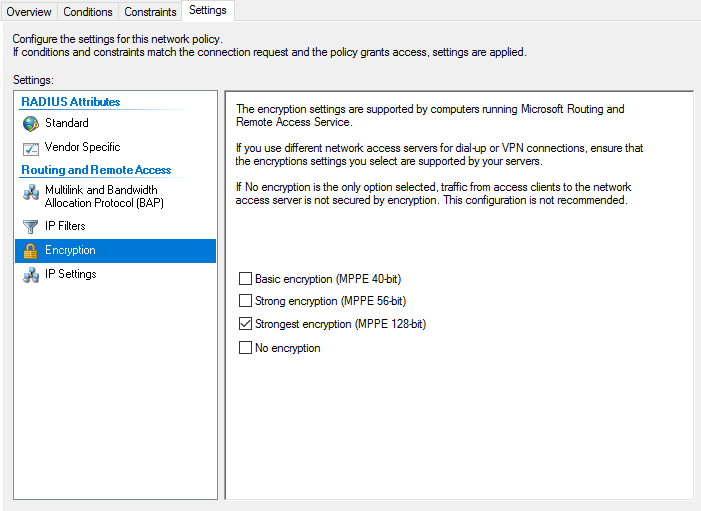
- Settings – Encryption: Make sure only Strongest Encryption (MPPE 128bit) is selected
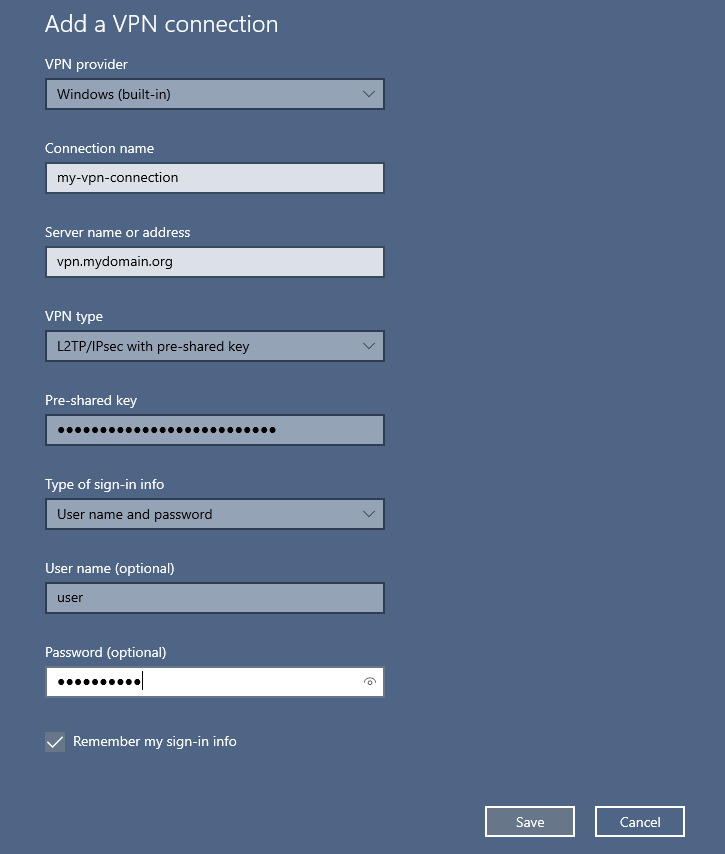
Step 4: Configure Windows 10 Client
Create a new VPN session with your windows client, make sure to select using a connection with a pre-shared secret key and user the credentials of your active directory user to connect.
e.g. DOMAIN.ORG\<USER> –> VPN USER: <USER>